Looking for a detailed guide on how to connect to your VPS with SSH and improve SSH safety for your server? This article has everything you need to know.
Introduction
As soon as you buy a new virtual private server (VPS) with one of our irresistible deals, you’ll probably want to log in and get started.
Secure Shell, most commonly referred to as SSH, is your go-to option for logging into your server.
In this tutorial, we'll cover basic SSH authentication, followed by ways of making logging in easier. Finally, we'll cover some easy-to-use strategies for improving the overall SSH Safety of your VPS.

Connecting to Your VPS with SSH - Prerequisites
You need a few things to log into your VPS server via SSH:
- A virtual private server running any of our OS options
- Your server’s IP address
- Your login/password credentials
- Your preferred SSH client
Step 1 - Finding Your VPS IP Address for SSH
You might not be familiar with all of the terms above, or where to find them. Let's quickly walk through your IP address, username/password, and what an SSH client is.
Your IP address is similar to the address to your home or apartment—it tells your computer "where" your server is on the internet. Your server's IP address can be easily discovered by logging into the SSD Nodes dashboard and clicking on Services or finding the appropriate active server by clicking Active under View in the left-hand navigation. Click on the specific server you want to log into. Then look for the IPv4 or IPv6 headings:
IPv4 xxx.xx.xx.xxx
IPv6 xxx:xx:xx:xx:xxx:xx:x
IPv4 vs IPv6
IPv4 addresses are 32-bit binary numbers, allowing for approximately 4.3 billion unique addresses. However, with the proliferation of internet-connected devices, IPv4 address exhaustion has become a significant concern due to the limited address space. IPv6 addresses, on the other hand, are 128 bits long, providing an astronomically larger pool of unique addresses.

What Port is SSH Using?

SSH, by default, uses port 22 for communication, acting like a specific door through which computers talk securely to each other over the internet. But it can be changed to any other available port. This flexibility allows users to enhance security by using non-standard ports.
Step 2 - Your VPS SSH Login Credentials
If this is your very first time logging in, you’ll be using the administrative account—also known as the Superuser—which is typed in as root.
This can be confirmed just beneath the IPv4 orIPv6 headings—you’ll also find your default password here.
Username root
Password xxxxxxxxxxxx
Step 3 - Choose Your Preferred SSH Client
On Linux and OS X computers, the default SSH client is OpenSSH, and should come pre-installed. There’s nothing more to install—you’re ready to go by opening a terminal using the ssh command.
On Windows, we recommend a free, open-source program called PuTTY. We recommend downloading the MSI installer to ensure you have all the necessary utilities to do more advanced techniques, like key-based logins.
Step 4 - Basic VPS SSH Login
By default, SSD Nodes servers are accessible through SSH, so you don’t need to spend any time on setup—just launch your favorite terminal emulator (Linux/OS X) and call the ssh command using the root user and the IP address you found above:
ssh root@IP_address
You might get a warning the first time you try connecting to your server—simply put, your computer just doesn’t recognize the remote server. You can safely type yes here—you won’t see the warning again.
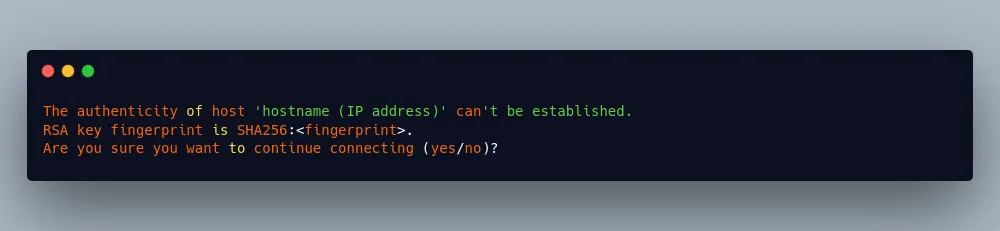
From here, you’ll be asked for your password—remember that it’s case sensitive!
At this point, you should be logged in and ready to take the next steps with your VPS and self host some awesome applications. If you need some advice about what you can do, check out our blog post What is Self-hosting?
The Putty-based Login
If you’re using a Windows machine, we recommend PuTTY to log in to your VPS. If it’s your first time launching PuTTY, you’ll be prompted with a configuration screen. Use the following configurations:
Host Name (or IP address): IP_address
Port: 22
Connection type: SSH
Click Open to begin the connection. If this is your first time, you’ll see a short warning. You can accept the connection by clicking Yes .
First, you’ll be prompted for a user account:
login as:
Enter root here. You’ll be prompted for your password.
Using keyboard-interactive authentication.
Password:
After this, you’ll be logged into a secure connection with your VPS.
If all you're interested in is logging in to your VPS via SSH, you'll be set at this point. Read on to learn more tips about how to create a non-root, sudo-enabled user, improve the security and safety of your SSH connection, and more.
Step 5 - Adding a New User
Right now, you’re logging into your server and performing all commands as the root user. This user has permissions to change every aspect of your server. This is good for the sake of administration, but regularly logging in and navigating your VPS as root isn’t great for security and SSH safety.
Instead, you should add a new user for the purposes of logging in and doing administrative work. Replace username with your preferred username.
adduser username
The command will ask you to input a password. We highly recommend a strong, secure password.
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfully
You’ll also be asked to input some other information. The default option is fine, so just hit Enter for each of these and then type Y to confirm.
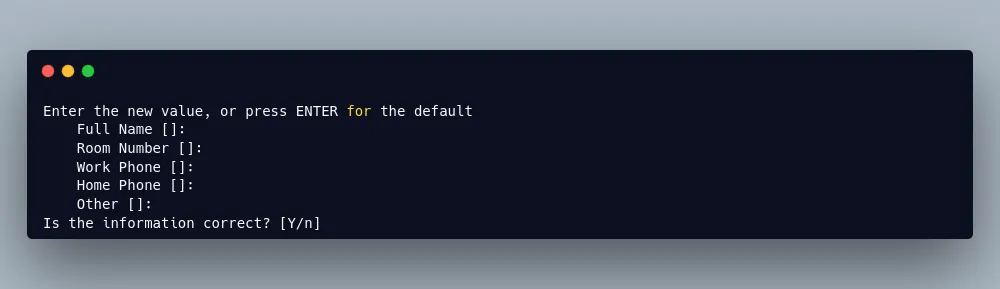
Add the new user to the sudo group.
usermod -aG sudo username
Before we can test out whether sudo access is working, we need to log into the user account.
logout
ssh username@remote_server
Now, make sure your sudo access is working. One way of doing this is by listing the /root/ directory, which is only possible with sudo access. You’ll be asked for your user’s password to authenticate.
sudo ls -la /root
[sudo] password for username:
Step 6 - SSH Safety on Your VPS

SSH safety is extremely important, and while SSH , by default, is a very secure method of connecting to remote servers, there are however some additional steps that you can take to further ensure the legitimacy of your connections.
Private SSH Authentication with SSH Keys
SSH keys are the easiest and best way to add additional security layers to your SSH connections.
SSH authentication involves a public key and a private key—the public key can be freely shared around the internet, while your private key should never be shared with anyone or brought outside your local machine. By placing your public key on your VPS, you can match up the public key with your private key to log in. This dramatically increases the security and safety of the connection—SSH keys are nearly impossible to attack via brute force.
Create the SSH Keys
First, create your keys on your local machine:
ssh-keygen -t rsa
You’ll be prompted with a request on where to save the newly-created files.
Enter file in which to save the key (/home/username/.ssh/id_rsa):
The best option here is to type Enter and place the keys in their default location. Next, you’ll be asked for a passphrase.
Enter passphrase (empty for no passphrase):
There are pros and cons to whether or not you choose to secure your SSH key with a passphrase. Passphrases offer increased security—even if a hacker gained access to your private key, they would also need to figure out your passphrase before they could use it against you. It’s almost like having two-factor authentication built into SSH.
The con of having a strong, secure passphrase is that you will be required to type it in every time you use your key. Consider all the variables for your application—if this is a personal server, no passphrase or a weaker passphrase may be sufficient. If your server is hosting user data, safety is of much greater importance.
You’ll be asked to enter the passphrase again, no matter your choice. The program will then give some additional output, and will create your keys. The public key (the one you may share) is located at /home/local-user/.ssh/id_rsa.pub . The private key is located at /home/local-user/.ssh/id_rsa .
If you want to create SSH keys on Windows using PuTTY, check out this guide .
Copy the SSH Key to Your Server
Now, you need to copy your public key to the VPS that you want to log into. The easiest way to do this is to use the ssh-copy-id program.
ssh-copy-id username@remote_server
If you don’t have that program available, you can also use the following command, which pipes the content of your public key file through SSH and appends the output to the end of the authorized_keys file on your server.
cat ~/.ssh/id_rsa.pub | ssh username@remote_server "cat >> ~/.ssh/authorized_keys"
You’ll see some output related to connecting to the server and copying your public key into the authorized_keys file on the VPS. Now you can try logging in with SSH again.
ssh username@remote_server
If you did not secure your SSH key with a passphrase, you’ll be immediately logged in. If you used a passphrase, SSH will ask for it. It’s important to remember that SSH is asking for your SSH key’s passphrase , not any of the user passwords you might have entered in earlier steps.
Disable Password-based Logins
Once you’ve ensured that you can log into your VPS with SSH keys, you can further improve SSH safety by disabling password-based logins for the root user and others.
Log into your VPS if you’re not already.
ssh username@remote_server
Open up the SSH configuration file in your editor of choice. nano is a user-friendly option for those newer to Linux administration.
sudo nano /etc/ssh/sshd_config
You’re looking for two lines: one that begins with PermitRootLogin and another that begins with PasswordAuthentication . Change them to the following:
PermitRootLogin no
PasswordAuthentication no
Finally, reload ssh to enable this change (for Ubuntu-based servers).
sudo systemctl restart ssh
Future logins will now be performed using your SSH key, and you won’t be able to directly log into the root account.
With any luck, all goes well and you’ll now be able to access your VPS easily and securely via SSH authentication.
Next, you can install the LAMP stack on your server, by following our Installing LAMP guide. You can also install LEMP with our LEMP tutorial, or even WordPress by going through How to Install WordPress with LEMP and MariaDB on Ubuntu 24.04!
A note about tutorials: We encourage our users to try out tutorials, but they aren't fully supported by our team—we can't always provide support when things go wrong. Be sure to check which OS and version it was tested with before you proceed.
If you want a fully managed experience, with dedicated support for any application you might want to run, contact us for more information.